Defining Copytrading
Copytrading is a server‑side process that replicates orders from one trading account to another according to predefined allocation rules. The follower selects a source account, sets a percentage or fixed‑lot size, and the platform transmits corresponding instructions when each trade is executed.

Machine‑learning models help evaluate and rank signal providers using metrics such as drawdown frequency, timing variance, and spread cost. These scores are descriptive indicators, not investment recommendations, and should be reviewed alongside manual analysis. The same algorithms can adjust allocation ratios in real time based on user‑defined volatility thresholds. Data governance standards ensure transparent sourcing of price feeds, outlier detection, and secure log archives. Community feedback loops aggregate anonymized user insights on latency or interface issues, guiding continuous improvements. Together, these components illustrate how AI supports, but does not replace, human decision‑making.
Platform risk controls include maximum daily loss limits, stop multipliers, and equity guards that suspend mirroring when capital falls below predefined levels. Technical interruptions, provider inactivity, or regulatory events can still impact order execution, so contingency planning is essential. Historical cases of partial fills and queue delays demonstrate how mirrored positions may diverge from their source.
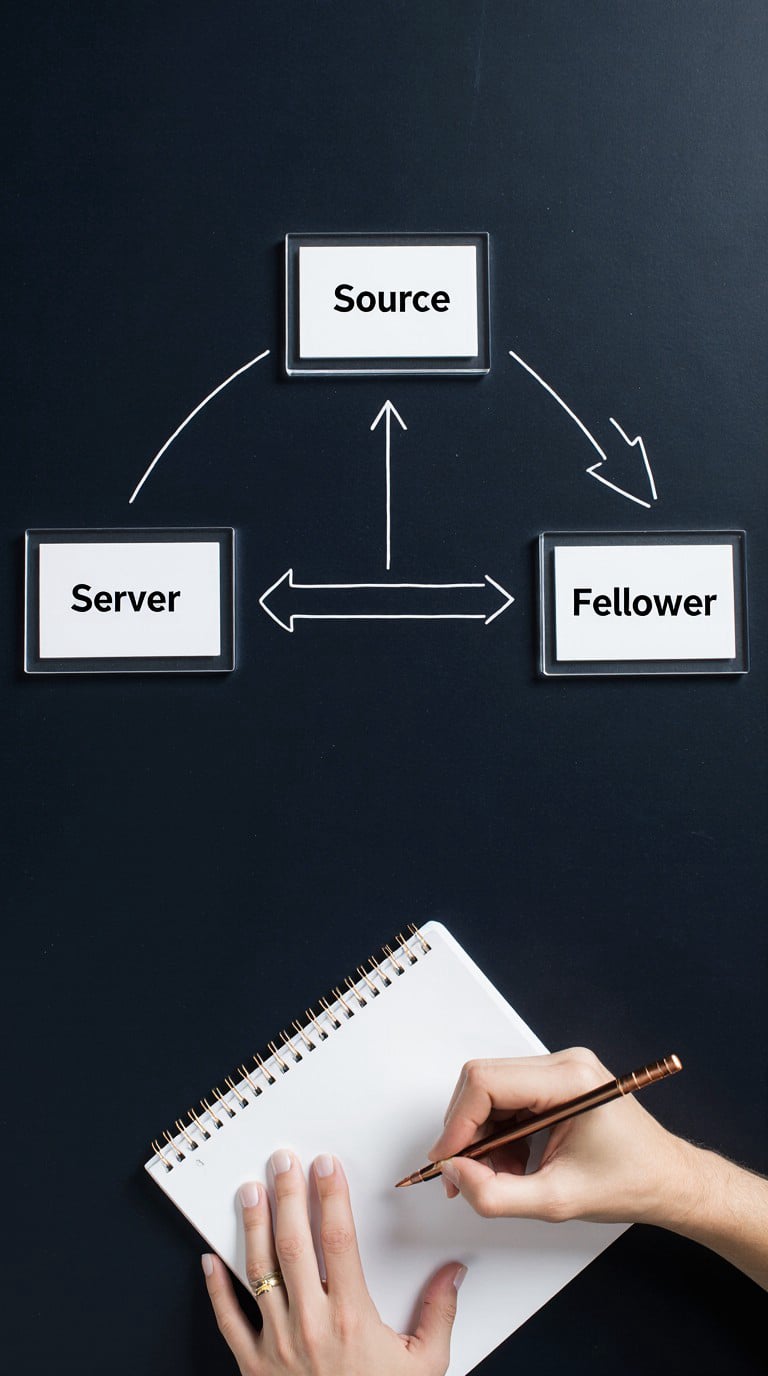
Copytrading platforms rely on globally distributed servers that route signals through low‑latency message queues before orders reach brokerage endpoints. Each stage—ingestion, validation, allocation—introduces measurable delay, so providers publish round‑trip benchmarks and maintain redundant nodes to minimize single‑point failures. Time‑stamped logs record every conversion from leader volume to follower allocation, enabling independent audits without revealing account details. Real‑time health dashboards track packet loss, queue depth, and processor load; thresholds trigger automatic rerouting to reserve nodes. By outlining this layered architecture, this resource clarifies how technical safeguards work under network stress while emphasizing that no system can eliminate all operational risk.